In an age where data breaches and cyberattacks are becoming increasingly sophisticated, the need for secure communication has never been greater. Enter quantum cryptography, a cutting-edge technology that promises to revolutionize the way we protect our information. In this blog, we will explore the fundamentals of quantum cryptography, its key principles, applications, and how it is set to transform the future of cybersecurity.
What is Quantum Cryptography?
Quantum cryptography is a method of secure communication that uses the principles of quantum mechanics to encrypt and transmit data. Unlike classical cryptography, which relies on complex mathematical algorithms to secure information, quantum cryptography leverages the unique properties of quantum particles to provide security that is theoretically unbreakable.
How Does Quantum Cryptography Work?
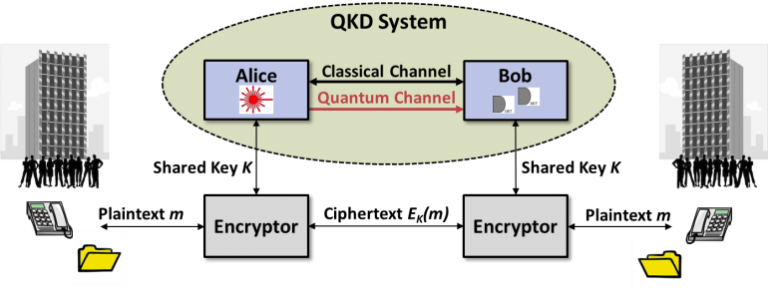
At the heart of quantum cryptography is the concept of quantum key distribution (QKD). QKD uses the quantum properties of particles, such as photons, to generate and share encryption keys between two parties. These keys are used to encrypt and decrypt messages, ensuring that only the intended recipient can read the information.
The most well-known QKD protocol is the BB84 protocol, developed by Charles Bennett and Gilles Brassard in 1984. This protocol uses the polarization states of photons to encode key information. The key advantage of QKD is that any attempt to eavesdrop on the key exchange will disturb the quantum states of the particles, alerting the communicating parties to the presence of an intruder.
Key Principles of Quantum Cryptography
Quantum Superposition and Uncertainty
Quantum cryptography relies on the principle of superposition, where particles exist in multiple states simultaneously until measured. This ensures that the exact state of a quantum particle is unknown until it is observed. Additionally, the Heisenberg Uncertainty Principle states that certain pairs of physical properties, like position and momentum, cannot both be precisely measured at the same time. This inherent uncertainty makes it impossible for an eavesdropper to measure the quantum key without introducing detectable anomalies.
Quantum Entanglement
Quantum entanglement is another key principle used in some quantum cryptography protocols. Entangled particles share a quantum state, meaning that the measurement of one particle instantly affects the state of the other, regardless of the distance between them. This property can be used to create correlated keys between two parties, providing a secure means of communication.
No-Cloning Theorem
The no-cloning theorem is a fundamental concept in quantum mechanics that states it is impossible to create an exact copy of an arbitrary unknown quantum state. This means that an eavesdropper cannot clone the quantum key without introducing errors, which would be detected by the communicating parties.
Applications of Quantum Cryptography

Quantum cryptography is more than just a theoretical concept; it has real-world applications that are already being explored and implemented.
Secure Communication Networks
One of the most promising applications of quantum cryptography is in the development of secure communication networks. These networks use QKD to provide end-to-end encryption that is immune to both classical and quantum attacks. For example, quantum cryptography is being used to secure government communications, financial transactions, and sensitive military data.
Quantum-Resistant Cryptography
As quantum computers become more powerful, they will be able to break many of the classical cryptographic algorithms currently in use, such as RSA and ECC. Quantum cryptography offers a quantum-resistant alternative, ensuring that sensitive data remains secure even in the face of quantum computing advancements.
Long-Distance Quantum Communication
Researchers are working on extending the range of QKD to enable long-distance quantum communication. This involves the development of quantum repeaters and satellite-based QKD systems, which can transmit secure keys over thousands of kilometers. China’s Micius satellite, launched in 2016, demonstrated the feasibility of satellite-based QKD, paving the way for a global quantum communication network.
Challenges and Limitations
While quantum cryptography offers unparalleled security, it is not without its challenges and limitations.
Technical Challenges
Implementing quantum cryptography requires highly specialized equipment, such as single-photon sources and detectors, which are expensive and difficult to manufacture. Additionally, maintaining the integrity of quantum states over long distances is challenging due to environmental factors like noise and decoherence.
Infrastructure and Scalability
Building a global quantum communication network requires significant infrastructure investment. Current QKD systems are limited in range and require a direct line of sight between the communicating parties. Scaling up these systems to cover large areas or connect multiple users remains a major hurdle.
Practical Considerations
Despite its theoretical security, quantum cryptography is not immune to all types of attacks. Side-channel attacks, where an attacker exploits information leakage from the physical implementation of a cryptographic system, could still pose a threat. Ensuring the practical security of quantum cryptographic systems requires continuous research and innovation.
The Future of Quantum Cryptography

Quantum cryptography is still in its early stages, but its potential to transform cybersecurity is immense.
Advancements in Quantum Technology
As quantum technology continues to evolve, we can expect significant improvements in the efficiency and cost-effectiveness of quantum cryptography systems. Researchers are exploring new QKD protocols, quantum repeaters, and integrated photonic chips that could make quantum cryptography more accessible and widespread.
Integration with Classical Systems
For quantum cryptography to achieve mainstream adoption, it will need to be integrated with existing classical cryptographic systems. Hybrid approaches, where quantum cryptography is used alongside classical methods, could offer a practical path forward, combining the strengths of both technologies.
Global Quantum Communication Networks
The ultimate goal of quantum cryptography is to enable a global quantum communication network that provides secure communication channels for everyone. This vision is already taking shape with projects like the European Quantum Communication Infrastructure (EuroQCI) initiative and China’s quantum satellite program. As these networks expand, they could fundamentally change the way we think about privacy and security in the digital age.
Conclusion
Quantum cryptography represents a new frontier in cybersecurity, offering a level of security that is fundamentally different from classical approaches. While there are challenges to overcome, the potential benefits of quantum cryptography are immense, making it a critical area of research and development. As we move towards a quantum future, the importance of secure communication will only continue to grow, and quantum cryptography will be at the forefront of this revolution.
Further Reading and Resources
For those interested in exploring the world of quantum cryptography further, here are some recommended resources:
- Books:
- “Quantum Cryptography and Secret-Key Distillation” by Gilles Brassard.
- “Quantum Computation and Quantum Information” by Michael A. Nielsen and Isaac L. Chuang.
- Research Papers:
- Bennett, C. H., Brassard, G. “Quantum cryptography: Public key distribution and coin tossing.” Proceedings of IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, 1984.
- Ekert, A. K. “Quantum cryptography based on Bell’s theorem.” Physical Review Letters, vol. 67, no. 6, 1991, pp. 661–663.
- Online Courses:
- edX: Quantum Cryptography – From Basics to Key Distribution.
- Coursera: Quantum Mechanics for Cryptographers.
FAQs
- What makes quantum cryptography more secure than classical cryptography?
- Quantum cryptography relies on the principles of quantum mechanics, such as superposition and entanglement, which provide security that is theoretically unbreakable by both classical and quantum computers.
- Can quantum cryptography be hacked?
- While quantum cryptography is highly secure, it is not immune to all forms of attacks. Side-channel attacks and practical implementation flaws could potentially be exploited, which is why ongoing research is crucial.
- Is quantum cryptography available for commercial use?
- Yes, quantum cryptography is already being used in some commercial applications, particularly in industries that require high levels of security, such as finance and government.